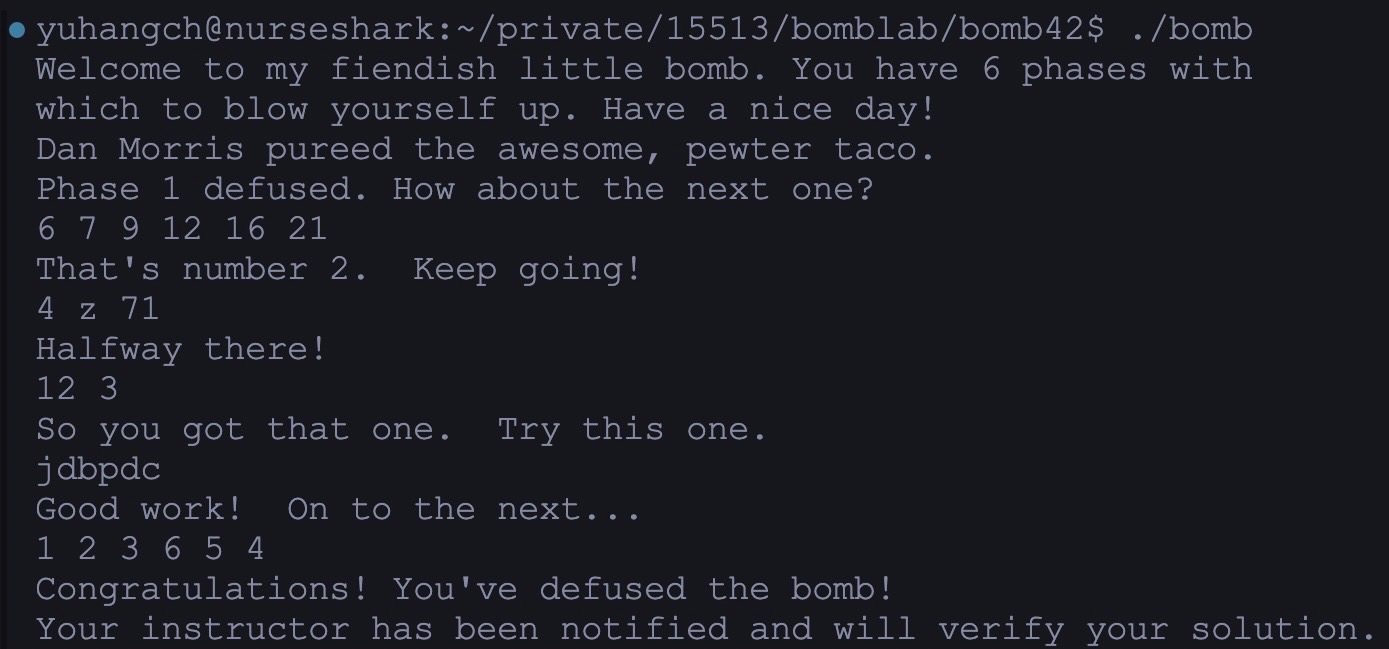
Bomb Lab
The Bomb Lab required me to defuse a binary bomb, a program composed of multiple phases, each demanding a specific string input. Incorrect inputs would result in the bomb "exploding," thereby terminating the program and signaling failure. The task was to analyze and understand the bomb's binary and assembly code to determine the correct inputs for each phase.
Below I will describe the technical skills and tools I've utilized.
Advanced Debugging with gdb
- Utilized gdb to step through the disassembled code, set breakpoints, and inspect both memory and register states.
- Developed a deep understanding of how the bomb processed inputs and learned to avoid unnecessary steps through library functions.
Code Analysis with objdump
- Employed objdump -t to explore the bomb's symbol table, identifying functions and variables that were critical to the bomb's operation.
- Disassembled the bomb's code using objdump -d, providing a detailed view of the assembly instructions and their interactions.
Completing the Bomb Lab significantly enhanced my skills in low-level programming, assembly language comprehension, and advanced debugging techniques. This experience not only bolstered my technical expertise but also prepared me for future challenges in computer systems and security.
- Binary Analysis
- Assembly Language
- Advanced Debugging
- gdb
- Code Disassembly
- Low-Level Programming
- System-Level Programming
- Software Security